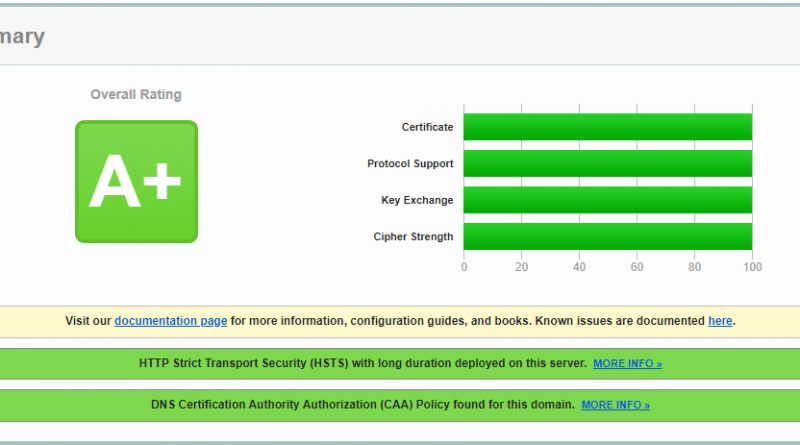
SSLLabs 100% in all sections Ubuntu Nginx and LetsEncrypt
#Certificate Section
Simple… just make sure your cert and chain are in the correct order and SHA256 certificates
#Protocol Support Section
TLS1.2 or stronger are necessary for
Needed entry in /etc/nginx/nginx.conf – http section
ssl_protocols TLSv1.2;
#KeyExchange
A few parts are necessary to reach this:
Part 1: Use a 4096-bit RSA or secp256 or higher Certifcate
Example (RSA):
_ certbot --rsa-key-size 4096 -(other-arguments) _
Part 2: Enable ecdh curves in Nginx (set in /etc/nginx/nginx.conf – http section)
ssl_ecdh_curve secp521r1:secp384r1;
Part 3: Somtimes Part 1 and 2 are enough, but also sometimes you need part 3 too –> stronger DHParam file –> see my post
#CipherStrength
Important is here that currently with activated TLS1.3 you wont get 100% SSLLabs Score.
Reason behind this that in OpenSSL there is still a 128bit cipher that prevents that. “Problem” is also that in the current TLS1.3 RFC this cipher is mandatory.
To reach the 100% Cipher Strength you have two Options:
Option 1: Manually remove this 128bit cipher from OpenSSL for TLS1.3 = you have a non RFC compliant TLS1.3 Webserver. Needed openssl.cnf is located at /usr/lib/ssl/openssl.cnf but i wont share a solution here to break an RFC 😉
Option 2: Don`t use TLS1.3 – is not a general recommendation from my side. just the hint if you want a 100% score
So my cipher section looks like this to reach the 100% cipher score:
Set in /etc/nginx/nginx.conf – http section
ssl_protocols TLSv1.2;
ssl_ciphers ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES256-GCM-SHA384;
ssl_prefer_server_ciphers off;